In an era where a single software glitch can cause sprawling disruptions, the recent CrowdStrike incident in July 2024 stands as a stark reminder of the fragile tapestry that our modern supply chains rely on. A seemingly innocuous code update that rippled through global IT infrastructures, paralyzing critical operations and unveiling vulnerabilities, transformed into a cautionary tale for investors and companies alike. This incident isn’t just a footnote in cybersecurity history; it’s a harbinger of the increasingly sophisticated nature of cyber threats that lurk in the shadows, quietly waiting to exploit our interconnected world.
Understanding CrowdStrike virus risks goes beyond headlines and delves deep into the psyche of investors who navigate the precarious waters of tech stock valuation. Whether you’re evaluating the potential return on a promising tech company or scrutinizing cybersecurity investments, it’s imperative to consider the broader implications of reputational damage, customer trust erosion, and recurring revenue fluctuations resulting from such incidents. In this guidepost, you’ll discover how a fragmented code line isn’t just a technical blip, but a significant factor that can sway market confidence and influence investment strategies, ultimately shaping the future landscape of the cybersecurity sector.
Unveiling the Vulnerabilities in IT Infrastructures
The July 2024 CrowdStrike code update debacle highlighted how a single oversight can cascade into a global outage. In this incident, a minor syntax error within an endpoint protection module propagated through thousands of enterprise networks, underscoring the challenges in supply chain cybersecurity. Modern IT infrastructures are built on layers of interdependent software—operating systems, hypervisors, security agents, and orchestration frameworks. Each layer represents a potential attack surface or failure point if security protocols and QA procedures aren’t airtight.
A critical takeaway from this episode is the need for real‐time monitoring and automated validation pipelines. Static code analysis and regression testing are necessary but no longer sufficient. Dynamic fault injection and chaos engineering practices—once the domain of cloud-native pioneers—must become standard in any mission-critical environment. Investors evaluating tech companies need to be attuned to how robust their continuous integration/continuous delivery (CI/CD) processes are. After all, the CrowdStrike virus risk wasn’t due to a novel malware strain but a mundane code omission. Yet the financial and operational fallout was anything but mundane.
Furthermore, we witnessed how interconnectivity amplifies software outage risks. Logistics platforms, healthcare record systems, and even aviation ground-handling software all relied on the compromised CrowdStrike update to safeguard their endpoints. When that protection faltered, entire supply chains stalled. From a financial standpoint, these ripple effects translate into lost productivity, remediation costs, legal liabilities, and share price volatility, factors that investors must incorporate in a comprehensive risk model.
Lessons Learned from the CrowdStrike Virus Risks
The CrowdStrike incident serves as a masterclass in risk management, reminding investors and IT leaders that no vendor or product is infallible. Despite CrowdStrike’s reputation for industry-leading threat intelligence, the episode revealed that operational glitches can be as damaging as zero-day exploits. Embracing a multi-layered defense strategy that includes redundancy, third-party penetration testing, and decentralized backup systems is non-negotiable in today’s threat environment.
Another lesson is the importance of transparency and rapid response. CrowdStrike’s swift acknowledgment and patch release helped contain the fallout, but stock prices still dipped by double digits. Market reactions are often driven by perception rather than technical nuance. Investors should track how a company communicates during crises, clear, data-driven updates signal competence, whereas opaque statements can fuel rumors and exacerbate reputational harm.
Lastly, the event underscores the value of integrating cybersecurity metrics into financial models. Quantify the probability and potential loss associated with software outage risks, and stress-test valuations against worst-case scenarios. By accounting for both direct remediation expenses and indirect revenue impacts, you transform abstract fears into actionable figures, enhancing the rigor of your CrowdStrike stock analysis and overall investing in cybersecurity stocks strategy.
Explore our most popular stock fair value calculators to find opportunities where the market price is lower than the true value.
- Peter Lynch Fair Value – Combines growth with valuation using the PEG ratio. A favorite among growth investors.
- Buffett Intrinsic Value Calculator – Based on Warren Buffett’s long-term DCF approach to determine business value.
- Buffett Fair Value Model – Simplified version of his logic with margin of safety baked in.
- Graham & Dodd Fair Value – Uses conservative earnings-based valuation from classic value investing theory.
- Intrinsic vs. Extrinsic Value – Learn the core difference between what a company’s really worth and what others pay.
- Intrinsic Value Calculator – A general tool to estimate the true value of a stock, based on earnings potential.
- Fama-French Model – For advanced users: Quantifies expected return using size, value and market risk.
- Discount Rate Calculator – Helps estimate the proper rate to use in any DCF-based valuation model.

Evaluating Tech Stock Valuation Post-Incident
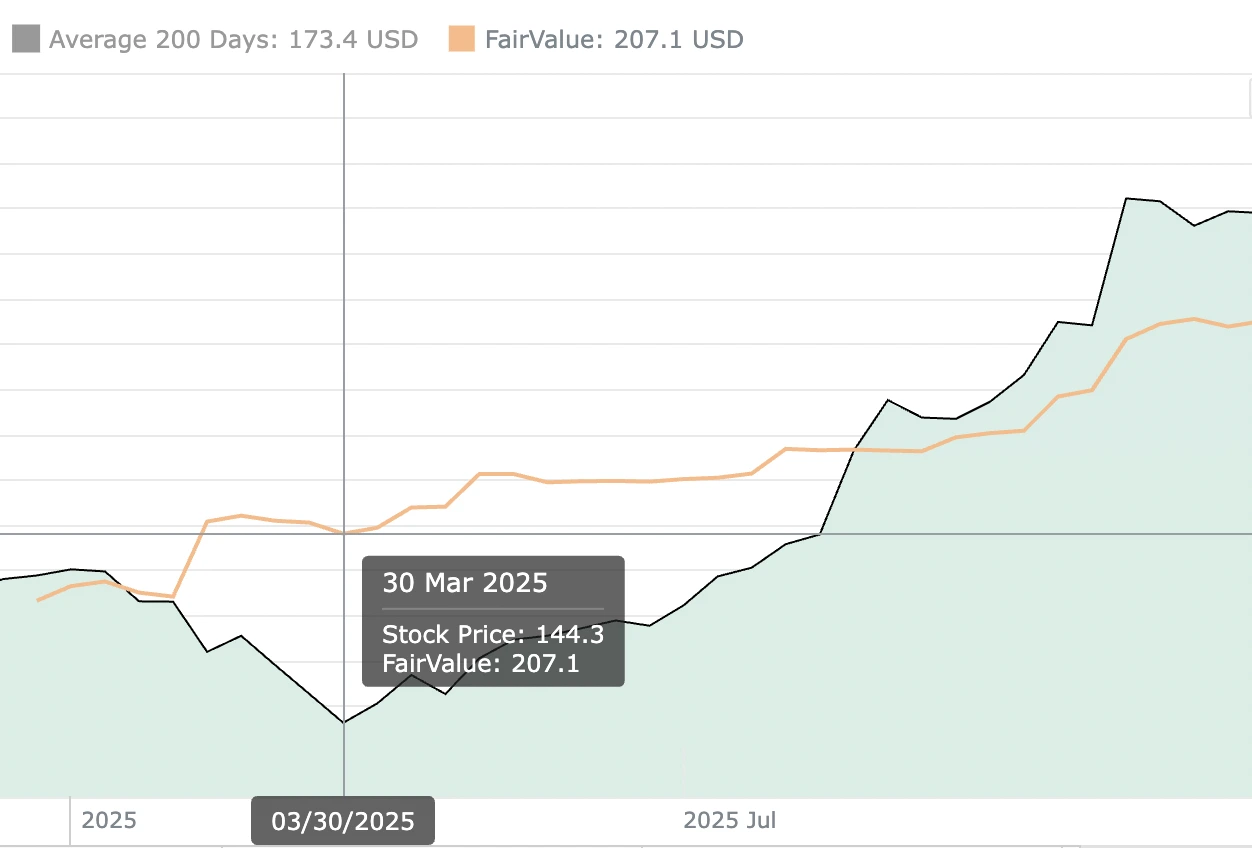
After a high-profile software failure, traditional valuation methods may underestimate the embedded cybersecurity liabilities. For companies like CrowdStrike, forward-looking multiples must factor in both the upside from recurring subscription models and the downside from single-point vulnerabilities. Discounted cash flow (DCF) analyses should include a probabilistic adjustment for remediation costs and potential customer churn tied to the CrowdStrike virus risk event.
Relative valuation also shifts post-incident. Peer multiples compress as market sentiment sours, creating buying opportunities for contrarian investors with a long-term horizon. However, due diligence must extend beyond headline P/E and EV/EBITDA ratios. Examine the percentage of revenue allocated to R&D, the rate of vulnerability patch deployment, and the resilience of partner ecosystems. Supply chain cybersecurity resilience can become a competitive moat if a firm invests sufficiently in automated threat detection and continuous compliance monitoring.
Analysts performing a CrowdStrike stock analysis now debate how much to penalize future growth forecasts for potential repeat incidents. While the market often overcorrects, persistent operational flaws can stoke recurring software outage risks. Investors should stress-test their models under multiple incident scenarios, one moderate glitch per year versus one severe breach every three years, and adjust their target prices accordingly.
Navigating the Fragile Tech Stock Market
Tech stocks, especially those in cybersecurity, are prized for high growth but are equally vulnerable to volatility spurred by software outages. The sudden spike in selling volume during the July 2024 CrowdStrike event reveals how quickly sentiment can shift. Investors should employ stop-loss orders and position sizing tactics to protect portfolios against sudden drawdowns triggered by software outage risks.
Another strategy involves diversification across sub-segments—endpoint security, cloud workload protection, SIEM, identity management—so that a vulnerability in one domain doesn’t tank your entire tech allocation. Following the CrowdStrike virus risk fallout, some investors discovered that their broad “cybersecurity” bucket was heavily skewed toward endpoint vendors. In response, they rebalanced toward network security and managed detection and response (MDR) services, which showed less correlation to single-vendor code failures.
Finally, consider layering your exposure with options strategies. Covered calls can generate income to offset minor valuation drops, while protective puts offer a hedge against extreme downside. When evaluating options on CrowdStrike or its peers, ensure implied volatilities reflect the latest incident data; overly low premiums signal complacency, whereas excessive spikes can make hedging cost-prohibitive.
💡 Discover Powerful Investing Tools
Stop guessing – start investing with confidence. Our Fair Value Stock Calculators help you uncover hidden value in stocks using time-tested methods like Discounted Cash Flow (DCF), Benjamin Graham’s valuation principles, Peter Lynch’s PEG ratio, and our own AI-powered Super Fair Value formula. Designed for clarity, speed, and precision, these tools turn complex valuation models into simple, actionable insights – even for beginners.
Learn More About the Tools →Reputational Damage: A Key Consideration for Investors
In the aftermath of a widespread outage, technology providers face a dual battle: remediation and reputation management. Stakeholders remember the downtime more vividly than the patch. When a CrowdStrike virus risk event unfolds, headlines often focus on business disruption, casting a shadow over the vendor’s brand equity. For investors, this reputational damage can translate into lower renewal rates and longer sales cycles as potential clients demand proof of enhanced safeguards.
Analysts should quantify reputational risk by tracking net promoter scores (NPS), customer satisfaction surveys, and third-party security ratings (e.g., BitSight, SecurityScorecard). A significant drop in these metrics post-incident can serve as a leading indicator of revenue deceleration. Moreover, social media sentiment analysis, using natural language processing tools, can capture the intensity and persistence of negative perceptions, which may not surface in quarterly earnings calls but can erode market share over time.
From a governance perspective, investors must scrutinize board oversight on cybersecurity. Firms with dedicated cyber risk committees and CISO accountability tend to recover more quickly. If CrowdStrike’s board lacked clear escalation protocols, that governance gap becomes a valuation liability. Conversely, companies demonstrating strong crisis management and transparent investor communications can turn reputational adversity into a competitive advantage, bolstering long-term returns.
Customer Trust Erosion and its Financial Implications
Trust is the currency of cybersecurity. Once enterprises question the reliability of protection software, renewing subscriptions or upselling additional modules becomes an uphill battle. The July 2024 CrowdStrike incident triggered a wave of customer inquiries and contract renegotiations, which temporarily depressed the company’s annual recurring revenue (ARR) growth. Investors must anticipate similar patterns in future CrowdStrike virus risk scenarios.
Measuring customer trust erosion requires a multi-pronged approach. Track churn rates month-over-month and compare against historical trends. Analyze average contract length adjustments and downgrades in seat counts. In the wake of the outage, some Fortune 500 firms shifted budgets toward internal open-source solutions or competitor offerings, reducing CrowdStrike’s net retention rate.
Financially, each percentage point increase in churn can shave off millions in ARR. For subscription models, lost future income streams are especially damaging because they compound year after year. Investors should incorporate a churn-based discount into their DCF models to account for the potential slide in renewal behavior following a high-profile software outage risk event.

Recurring Revenue Fluctuations in the Wake of Cybersecurity Threats
Cybersecurity vendors tout the appeal of predictable, subscription-based revenue. Yet when the threat focus shifts from random malware to internal code errors, those steady cash flows can wobble. The CrowdStrike virus risk episode showed that even best-in-class providers must contend with sudden dips in bookings and deferred renewals. Understanding the seasonality and incident-driven variability in bookings is crucial for accurate revenue forecasting.
Smart investors dissect the breakdown between new bookings, upsells, and renewals. If upsells stall or new logo acquisition slows post-incident, it signals deeper trust issues, not just temporary investor jitters. Moreover, deferred revenue liabilities can balloon as clients delay payments pending “all clear” notices. Monitoring deferred revenue schedules and days-sales-outstanding (DSO) trends provides clarity on how quickly the vendor can rebound to normalized cash generation levels.
Finally, examine how vendors structure SLAs and service credits. Generous credit provisions may pacify upset clients but at the cost of margin erosion. In the case of CrowdStrike, the company waived certain fees and offered extended trial periods to placate affected customers, an approach that protected customer relationships but weighed on near-term profitability.
Shaping Investment Strategies in the Cybersecurity Sector
Given the heightened focus on CrowdStrike virus risk, investors should refine their playbooks when allocating to cybersecurity. First, distinguish between pure-play security firms and diversified tech giants with in-house security units. The latter often leverage broader resources to mobilize emergency patches, whereas pure-plays may face capacity constraints in critical moments.
Second, prioritize companies with robust bug-bounty programs and transparent vulnerability disclosure policies. These initiatives demonstrate a proactive stance on supply chain cybersecurity and reduce the likelihood of hidden code flaws. In your analysis, assign a valuation premium to firms that publish regular transparency reports and maintain active public bug-bounty bounties.
Third, consider thematic ETFs to spread idiosyncratic risks. Products that track a basket of leading cybersecurity names can mitigate the fallout from any single vendor’s software outage risks. Complement these broad positions with selective direct investments in high-growth disruptors that focus on emerging vectors—IoT security, cloud-native posture management, and zero-trust network access solutions.
Conclusion: Looking Ahead in the Landscape of Cybersecurity Investments
The July 2024 CrowdStrike virus risk incident illuminated the thin line between security confidence and operational catastrophe. Investors must now weave software outage risks and supply chain cybersecurity considerations into every valuation model. Far from a niche concern, these factors shape the revenue trajectory and market positioning of cybersecurity vendors.
Moving forward, rigorous due diligence on governance, resilience protocols, and customer sentiment will distinguish savvy investors from the herd. By stress-testing portfolios against hypothetical code errors and supply chain disruptions, you can navigate the fragile tech stock market with greater conviction and capture upside in an increasingly threat-aware world.